Gaza death toll exceeds 75,000 as independent data verify loss | Israel-Palestine conflict
The true human cost of Israel’s genocidal war on the Gaza Strip has far exceeded previous official estimates, with independent research published in the world’s leading medical journals verifying more than 75,000 “violent deaths” by early 2025.
The findings, emerging from a landmark series of scientific papers, suggest that administrative records from the Gaza Ministry of Health (MoH) represent a conservative “floor” rather than an overcount, and provide a rigorous bedrock to the scale of Palestinian loss.
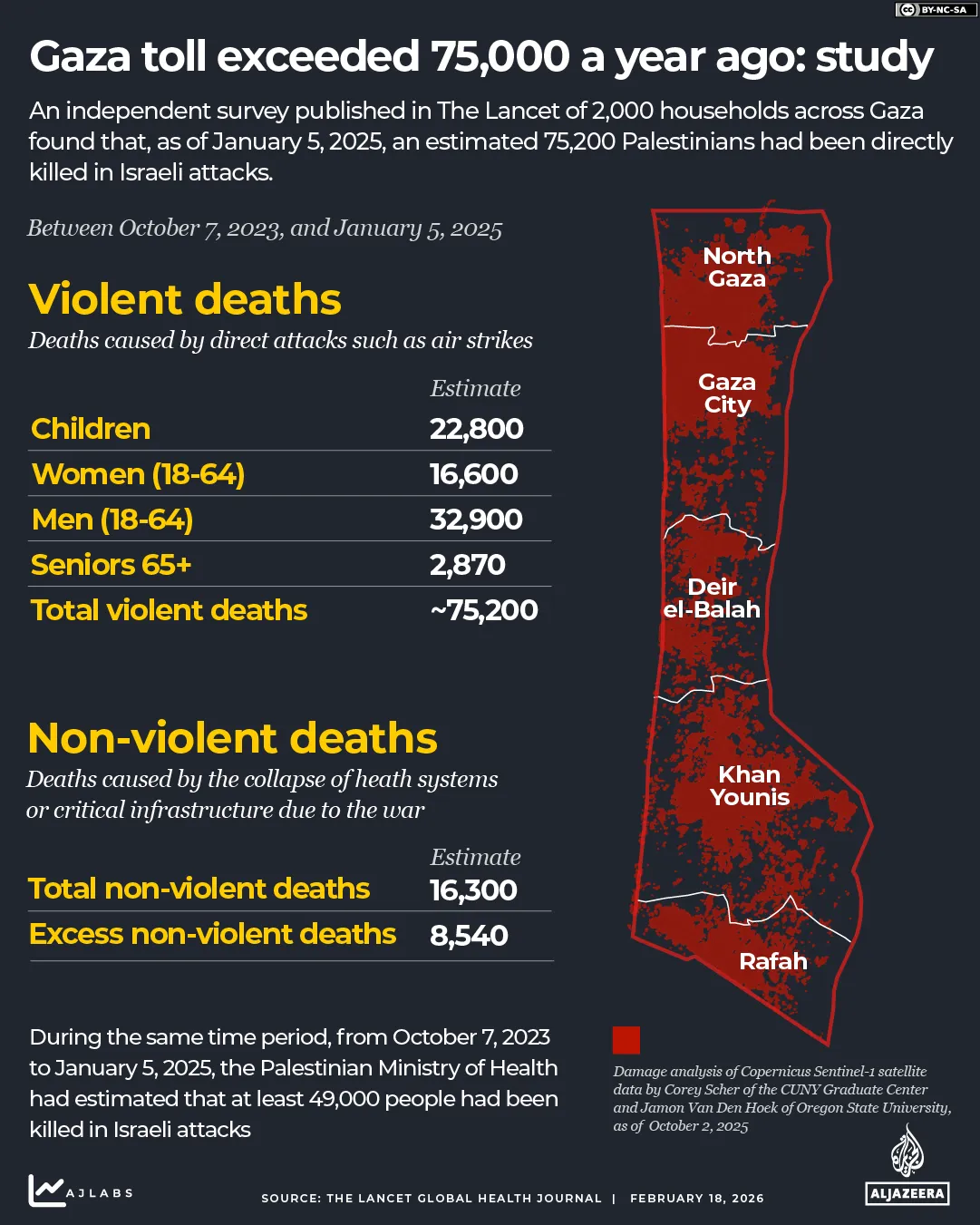
The Gaza Mortality Survey (GMS), a population-representative household study published in The Lancet Global Health, estimated 75,200 “violent deaths” between October 7, 2023 and January 5, 2025. This figure represents approximately 3.4 percent of Gaza’s pre-conflict 2.2 million population and sits 34.7 percent higher than the 49,090 “violent deaths” reported by the MoH for the same period.
The Gaza Health Ministry estimates that as of January 27 this year, at least 71,662 people have been killed since the start of the war. Of those, 488 people have been killed since the declaration of a ceasefire in the Gaza Strip on October 10, 2025.
Israel has consistently questioned the ministry’s figures, but an Israeli army official told journalists in the country in January that the army accepted that about 70,000 people had been killed in Gaza during the war.
Despite the higher figure, researchers noted that the demographic composition of casualties – where women, children, and the elderly comprise 56.2 percent of those killed – remains remarkably consistent with official Palestinian reporting.

Scientific validation of the toll
The GMS, which interviewed 2,000 households representing 9,729 individuals, provides a rigorous empirical foundation for a death toll.
Michael Spagat, a professor of economics at Royal Holloway University of London and the study’s lead author, found that while MoH reporting remains reliable, it is inherently conservative due to the collapse of the very infrastructure required to document death.
Notably, this research advances upon findings published in The Lancet in January 2025, which used statistical “capture-recapture” modelling to estimate 64,260 deaths during the war’s first nine months.
While that earlier study relied on probability to flag undercounts, this report shifts from mathematical estimation to empirical verification through direct household interviews. It extends the timeline through January 2025, confirming a violent toll exceeding 75,000 and quantifying, for the first time, the burden of “non-violent excess mortality”.
According to a separate commentary in the same publication, the systematic destruction of hospitals and administrative centres has created a “central paradox” where the more devastating the harm to the health system, the more difficult it becomes to analyse the total death toll.
Verification is further hindered by thousands of bodies still buried under rubble or mutilated beyond recognition. Beyond direct violence, the survey estimated 16,300 “non-violent deaths”, including 8,540 “excess” deaths caused directly by the deterioration of living conditions and the blockade-induced collapse of the medical sector.
Researchers highlighted that the MoH figures appear to be conservative and reliable, dispelling misinformation campaigns aimed at discrediting Palestinian casualty data. “The validation of MoH reporting through multiple independent methodologies supports the reliability of its administrative casualty recording systems even under extreme conditions,” the study concluded.
A decade of reconstructive backlogs
While the death toll continues to mount, survivors face an unprecedented burden of complex injury that Gaza’s decimated healthcare system is no longer equipped to manage. A predictive, multi-source model published in eClinicalMedicine quantified 116,020 cumulative injuries as of April 30, 2025.
The study, led by researchers from Duke University and Gaza’s al-Shifa Hospital, estimated that between 29,000 and 46,000 of these injuries require complex reconstructive surgery. More than 80 percent of these injuries resulted from explosions, primarily air attacks and shelling in densely populated urban zones.
The scale of the backlog is staggering. Ash Patel, a surgeon and co-author of the study, noted that even if surgical capacity were miraculously restored to pre-war levels, it would take approximately another decade to work through the estimated backlog of predicted reconstructive cases. Before the escalation, Gaza had only eight board-certified plastic and reconstructive surgeons for a population exceeding 2.2 million people.
The collapse of the health system
The disparity between reconstructive need and capacity is exacerbated by what researchers describe as the “systematic destruction” of medical infrastructure. By May 2025, only 12 of Gaza’s 36 hospitals remained capable of providing care beyond basic emergency triage, with approximately 2,000 hospital beds available for the entire population, down from more than 3,000 beds before the war.
“There is little to no reconstructive surgery capacity left within Gaza,” the research concluded, warning that specialised expertise like microsurgery is almost absent. The clinical challenge is further compounded by Israel’s use of incendiary weapons, which produce severe burns alongside blast-related fractures.
The long-term effect of these injuries is often irreversible. Without prompt medical treatment, patients face high risks of wound infection, sepsis, and permanent disability. The data indicate that tens of thousands of Palestinians will remain with surgically addressable disabilities for life unless there is a huge international increase in reconstructive capacity and aid.

The ‘grey zone’ of mortality
Writing in The Lancet Global Health, authors Belal Aldabbour and Bilal Irfan observed a growing “grey zone” in mortality where the distinction between direct and indirect death becomes blurred. Patients who die of sepsis months after a blast, or from renal failure after a crushing injury because they cannot access clean water or surgery, occupy a space that risks understating the true lethality of military attacks.
Conditions have only deteriorated since the data collection periods. By late 2025, forced evacuations covered more than 80 percent of Gaza’s area, with northern Gaza and Rafah governorates facing full razing by Israeli forces. Famine was declared in northern Gaza in August 2025, further reducing the physiological reserve of injured survivors and complicating any surgical recovery.
This series of independent studies serves as an urgent call for accountability and an immediate cessation of hostilities. “The healthcare infrastructure in Gaza is being repeatedly decimated by attacks despite protection by international humanitarian law,” researchers stated. They underscored that the only way to prevent the reconstructive burden from growing further is an immediate end to attacks against civilians and vital infrastructure.