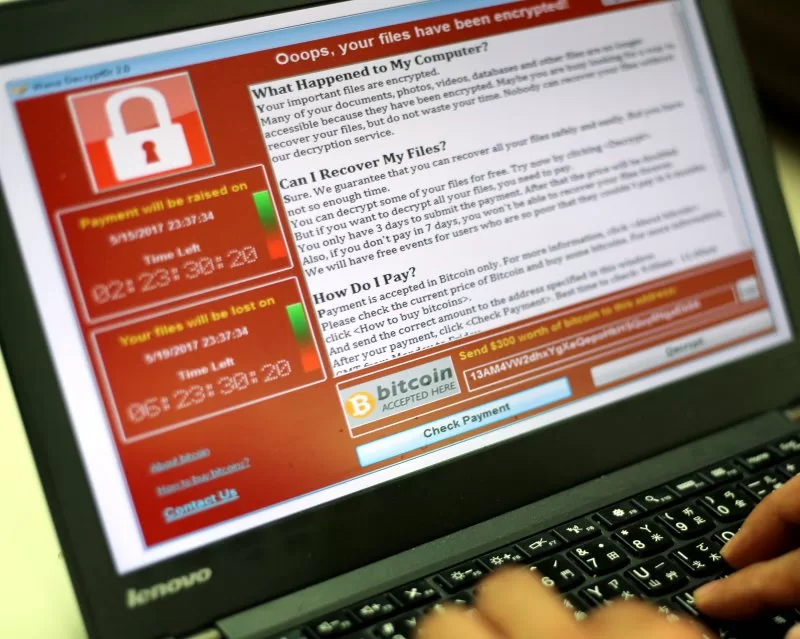
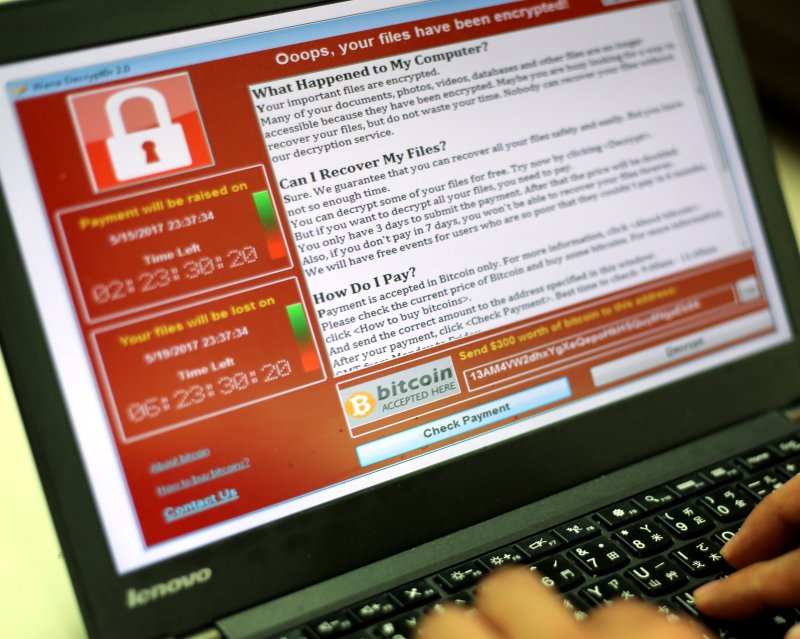
1 of 2 | A programer shows a sample of a ransomware on a laptop in Taipei, Taiwan (2017). On Monday, the U.S. Department of State and the Secret Service announced that they are offering up to $2.5 million for information leading to the arrest and/or conviction of Volodymyr Kadariya, a 38-year-old Belarusian citizen wanted in the United States for his alleged participation in a significant malware organization.
File Photo by Ritchie B. Tongo/EPA-EFE
Aug. 26 (UPI) — The U.S. government is offering up to $2.5 million for information leading to the arrest and/or conviction of Volodymyr Kadariya, a 38-year-old Belarusian citizen wanted in the United States for his alleged participation in a significant malware organization.
The Department of State and Secret Service announced Monday they are jointly offering the reward.
Kadariya, aka Volodymyr Kadaria or Vladimir Kadaria, is charged with cybercrime offenses associated with an alleged scheme to transmit the Angler Exploit Kit, as well as other malware and online scams to computers of millions of unsuspecting Internet users through online advertisements — so-called “malvertising.” It occurred from October 2013 through March 2022.
He was indicted on June 14, 2023, in the District of New Jersey. The U.S. Attorney’s Office in New Jersey unsealed the indictment on Aug. 12.
Kadariya was indicted along with Maksim Silnikau, a 38-year-old Belarusian and Ukrainian dual national, and Andrei Tarasov, 33, a Russian national, on the cybercrime charges.
Silnikau was extradited from Poland.
They face maximum penalties of 27 years in prison for wire fraud conspiracy, 10 years in prison for computer fraud conspiracy, and 20 years in prison on each wire fraud count.
The AEK was a leading vehicle through which cybercriminals delivered malware onto compromised electronic devices at times during the scheme, the Secret Service said.
“The malvertising campaigns were designed to appear legitimate, but often redirected victim Internet users who viewed or accessed the advertisements to malicious sites and servers that sought to defraud the users or delivered malware to the users’ devices,” Secret Service officials said.
Kadariya and his co-conspirators also allegedly sent “scareware” ads that displayed false messages claiming to have identified a virus or other issue with a victim’s Internet device. Victims were deceived into buying or downloading dangerous software, providing remote access to the device, or disclosing personal identification or financial information.
Accounts on predominantly Russian cybercrime forums allegedly were used to sell access to the compromised devices used by victims, as well as victims’ banking information and login credentials.
“Cybercriminals should know that even if they attempt to hide their criminal conduct behind the anonymity of the internet that eventually, through the dedication of international law enforcement professionals, they will be apprehended and held accountable for their actions,” Brian Lambert, the Secret Service’s assistant director of investigations, said in a news release on Aug. 12.
The reward was authorized under the Department of State’s Transnational Organized Crime Rewards Program, which supports law enforcement efforts to disrupt transnational crime globally and bring fugitives to justice.
People with information about Kadariyacan contact the U.S. Secret Service by email at [email protected] or visit visit the nearest U.S. Embassy or Consulate.