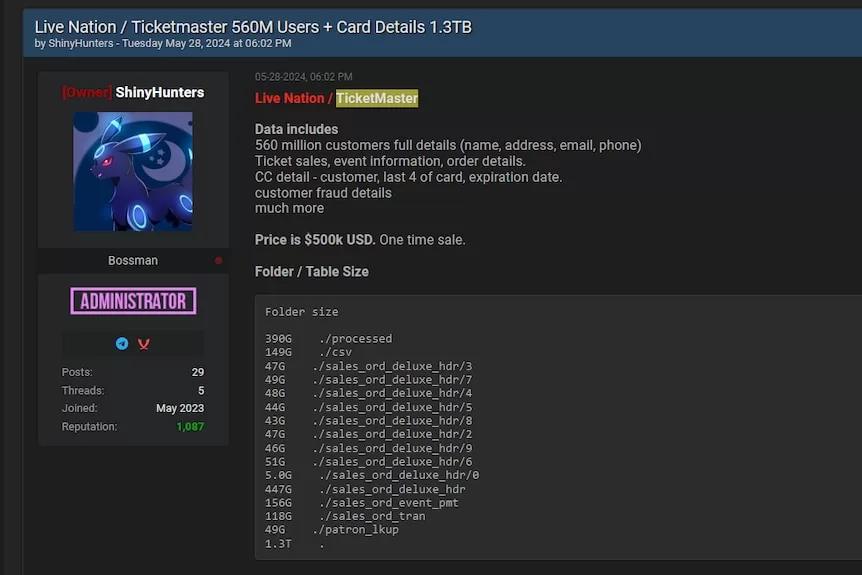
In an online forum on the dark web, the hacker group ShinyHunters are right now spruiking what they say is 1.3 terabytes of Ticketmaster customer data.
Using the avatar of the “shiny” blue Umbreon Pokémon, the group operates much like players in the animated game.
Driven by the aim to “Catch ’em all!”, instead of hunting and collecting Pokémon characters, the cyber criminals steal and resell as much data as they can.
And ShinyHunters appear to be aiming for the high score.
The international syndicate is allegedly behind some of the most notable, high-profile breaches of vast databases in recent years.
And now they claim to be in possession of the personal details of 560 million global Ticketmaster customers — and are hawking it for $US500,000 ($750,000).
This is what we know about what authorities have called a “remarkably devious” group.
Data breach sprees
When ShinyHunters emerged in 2020, the group immediately set out to make a name for themselves.
Across two weeks in May, they went on a data breach spree, claiming to have targeted more than a dozen companies, stealing over 200 million customer records.
That included about 91 million user accounts from Indonesian e-commerce company Tokopedia, and data from Microsoft’s GitHub.
In 2021, they swiped the records of more than 70 million customers at US telco AT&T.
And nearly 200,000 Pizza Hut customers in Australia had their information stolen in a cyber attack in September last year, allegedly carried out by the group.
A French citizen was arrested in Morocco in 2022 for his involvement in ShinyHunters.
The now 22-year-old, Sebastien Raoult, was extradited to the US and sentenced to three years in prison earlier this year.
He was also ordered to pay more than $US5 million in restitution.
US authorities said he was involved in the group’s activities over two years and was motivated by “pure greed”.
“The lengths to which Mr Raoult and his co-conspirators went to steal personal and financial information are remarkably devious, and he played a substantial part,” Richard Collodi, Federal Bureau of Investigation (FBI) Seattle special agent, said.
David Tuffley, a cybersecurity expert from Griffith University, said ShinyHunters were a well-established group who certainly aren’t shy about taking credit for their crimes.
But they communicate in highly encrypted channels and could be operating from anywhere.
“So even if one individual is apprehended, there’s still many out there,” he said.
“Unfortunately, they are getting better organised all the time … It’s just too difficult to crack into that network.”
Hawking data on their own marketplace
ShinyHunters promoted the sale of the Ticketmaster data on a dark web forum it was known to previously operate.
The forum — a marketplace for stolen data to be leaked and sold — had recently been seized and taken down by the US FBI.
But it appears to have re-emerged with a post from the group claiming it has names, addresses, credit card numbers, phone numbers and payment details of Ticketmaster customers.
But the authenticity of the post and data is difficult to verify.
Open-source intelligence researcher CyberKnow has warned the leak contains “some questionable aspects”, and the volume and nature of the breach may be “over-stated to boost attention”.
It says it could be a PR stunt for what appears to be the rebooted forum.
It is the same forum where a hacker threatened to release the personal data of about 10 million Optus customers before retracting the post.
The Department of Home Affairs has confirmed it is on the case, but Ticketmaster is yet to publicly comment.
“It is troubling that Ticketmaster has not made any public statements regarding this data breach,” Professor Nigel Phair from Monash University’s department of cybersecurity said.
“There are over five million Australian and New Zealand Ticketmaster account holders, they will be concerned about any loss of personal information, including names, addresses, passwords, credit card numbers, etc. and where this may end up on the dark web.”
What happens to the data?
Generally, hackers ask for a ransom in order to not release the data, but Dr Tuffley says they often go on to sell it on the dark web anyway.
In terms of paying a ransom, the advice is always never to pay.
“It just sustains that business model, and it’s quite likely that you won’t get your data back anyway,” he said.
That model, he says, usually begins with cyber criminals selling email addresses.
Those email addresses are sent spam, which these days are “carefully calculated to get the recipient to click on a link” that infects a computer with malware.
“It then acts to sort of freeze everything and before the person knows that their system has ground to a halt, and then they’re getting a ransom demand,” Dr Tuffley said.
When certain data is leaked there is also the potential risk of identity fraud, or information to be used for phishing or impersonation attacks.
Dr Tuffley says hackers would need to “hit the jackpot” to get enough information from one data breach to be able to open a bank account using a stolen identity.
How are ShinyHunters getting big businesses?
US authorities detailed some of the group’s tactics when Raoult was sentenced.
They said he helped create websites that pretended to be login pages belonging to legitimate businesses.
ShinyHunters then sent phishing emails to company employees with links to those pages, which enabled them to steal log-in data and access information on company networks and third-party providers.
“The conspirators stole hundreds of millions of customer records and caused loss to victim companies that is estimated to exceed $6 million,” the US Attorney’s Office said in a statement.
Dr Tuffley says although these organisations have good defences, all they need to do is convince one person to click on a link.
He described it as a “social engineering attack”, saying nine out of 10 of these breaches happen that way.
“An organisation can have really solid defences, but if people in the organisation make the mistake of clicking on that link, then it sort of negates all those defences,” he said.
However, there are steps organisations can take to ensure data is better protected.
Matthew Warren, the director of the RMIT Centre for Cyber Security Research and Innovation, said the Ticketmaster attack highlights our new cyber normal.
And if steps are not undertaken to improve their cyber security then the situation will be repeated time after time.
“Once the data has been stolen from the organisation there is nothing that the organisation can do to protect the data,” Professor Warren said.
“If the organisation had encrypted the data, then if the data had been stolen, it would have been unusable by the hacker.”
Consumers who believe they may have been caught up in the breach are being advised to be on the lookout for unusual emails, SMS or phone calls.
They are also being told to look for any suspicious credit card transactions.